Creating a hidden, whitelisted server
This guide will cover basic steps to set up a hidden whitelisted server aimed at advanced users with root access, it will not cover installation.
The purpose of this guide is to help server owners avoid Denial of Service (DoS) attacks and the server being discovered publicly.
Rust by default doesn't offer a whitelisting system but does have skipqueue, see the Whitelisting section below.
Requirements
- Strong knowledge of server hosting
- Knowledge of Rust server installation
- Knowledge of Oxide/Umod installation
- Knowledge of Windows/Linux firewall-config
- Dedicated server with administrator/root access
Server Hosting
While this guide will advise on remaining hidden it's strongly recommended you use the best server hosting around with the ability to change IPs quickly, strong DDoS protection and no null routing.
Facepunch uses OVH "GAME" servers for years with great success and comes highly recommended for this guide. It's important to note we're also using a dedicated server environment for this guide.
Despite following all recommendations on this guide, it's extremely likely that there will be a server IP leakage at some point in time.
To be prepared for this eventuality, it's advised you prepare multiple IP addresses in advance to quickly switch to in the event of a leakage. This includes the firewall setup described in other sections below.
Depending on the hoster (for this guide we're using OVH as a basis) you're usually able to order multiple IPv4 addresses at large quantity.
Once ordering the IP addresses, make sure to bind them to the operating system you're using.
What defines an IP leakage
It's suggested you change your server IP address following the instructions outlined in the previous segment upon a server leakage if you experience any of the events below:
- A streamer shows the IP address by mistake to viewers
- A random player who's associated with no one attempts to connect
- The server is being attacked via DDoS (most network providers email you when this occurs)
- Network traffic is abnormally large or has intermittent large spikes (differences of more than 100Mbps)
Ports
It's highly advised to use nonstandard ports, this will help prevent server list scrapers from accessing your information.
Steam queryport
The Steam queryport should be blocked at all times otherwise the server can be discovered and seen within the Steam master server list and within RUST server listings.
This is the port that responds to the Steam queries, which is what Rust and other third party applications use to populate server information. This can include but is not limited to: server name, server player count, map information and active players.
You can easily avoid this information being public by setting the queryport to something obscure which you can later refuse traffic to using a firewall.
For example, if you set your queryport to 65000 you will need to reject UDP & TCP to port 65000 on the IP address that you're using for the server.
Whitelisting
For making a server truly private, you'll want to set up a whitelisting system. This is where the prerequisite of Oxide/uMod installation comes from.
You'll need Oxide/uMod for this process. We recommend using this publicly available community made add-on here after installing: https://umod.org/plugins/whitelist
You will place this in your plugins folder and the plugin should load.
Once installed, you can whitelist participants of the server using o.grant user <id> whitelist.allow. <id> is the Steam 64 id of a given participant.
A simpler alternative method
Use the built in Skip Queue. Set server.maxplayers to 0, any admin, or user with skip queue will still be able to join. Add a user to skip queue with global.skipqueueid <id> [name] [note]. These go into the users.cfg file similar to admins.
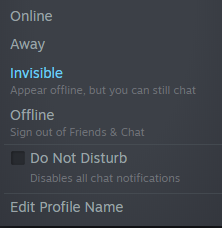
User's Visibility
At all times users should be set to "Invisible" on Steam as not to display the Game, IP and port on their Steam profile.
Users Connecting
It's common for content creators to accidentally show sensitive information on live streams so it's highly recommended connecting to a server via keybinds:
Bind this 'off-stream' / 'out of view of viewers' (F1 command)
The streamer will just need to press F6 from the main menu to connect thereafter and never leak server info.
Other helpful Server Commands
| Command | Description |
|---|---|
| censorplayerlist true | This will mask the player names being accessible by 3rd party applications scraping server lists. |
 Garry's Mod
Garry's Mod
 Rust
Rust
 Steamworks
Steamworks
 Wiki Help
Wiki Help